Inbox Security And Protecting Your Data
Take a second and imagine what would happen if you suddenly lost all of your emails. What if an employee clicked a link that, in literally less than a second, wiped the data from all the computers on your network? Talk about a pull-your-hair-out nightmare. The good news is that protecting your inbox and your data can cost as low as $5 a month!
Every day, hackers wind up in the inboxes of people and businesses, and their emails are getting more and more difficult to spot. Our CEO, James, has recently received phishing emails disguised as emails from RBC, Amazon, and Canada Post – and even he had to admit they were good attempts at mimicking the real thing.
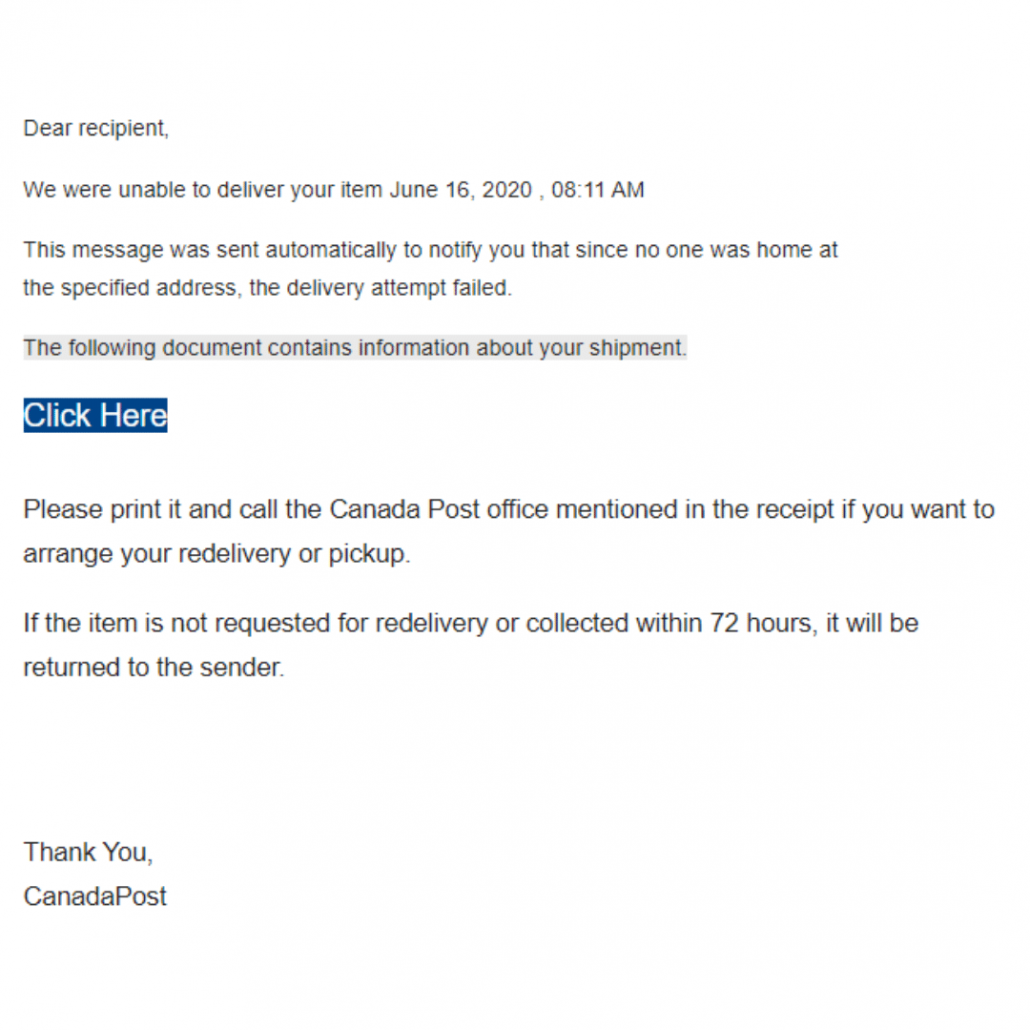
These emails contain links or attachments that download viruses that work incredibly quickly. By the time someone clicks the link and sees a screen pop-up, the damage is already done and it’s possible the entire office will be infected.
But it’s not just hackers sending in viruses via emails that land in your inbox. They’re also breaking into email accounts and wreaking havoc by encrypting everything or adjusting settings. We’ve seen cases where hackers have created a rule that forwards your emails to someone else, or sends everything directly to the Trash folder – and all you know is that you’re not getting emails!
It’s crucial to have two-factor authentication set-up to help prevent scenarios like this. Hackers are not sitting at a computer manually entering passwords hoping something works, they have programs that cycle through combinations at incredible rates.
Luckily, there are systems we can put in place to help you reduce the risk and keep your data and inbox protected. We focus on three main tactics:
- Filtering: First things first we recommend putting a filter on your inbox to keep the spam and phishing attempts out of your mailbox to begin with.
- Protecting: Setting up two-factor authentication requires the user to confirm on their cell phone that they are in fact the person attempting to log-in. It can be a hassle sometimes, but the inconvenience is by far less than that of a hacker successfully getting into your inbox.
- Back-up: If you lose everything in your inbox, Microsoft and Google can sometimes get you back the last 30 days of emails. But, it’s not their job and if they can’t, they aren’t too bothered about it. We can put recovery systems in place that get you back your emails – worst case scenario, we can at least get you back to the day prior.
For about the price of a Starbucks latte, you can have peace of mind that your inbox is protected and your data is safe. Give us a call today to chat about getting this set up: (514) 634-INFO (4636) x 101








